How to Tell What Is Using Bandwidth on Network
A Step-Past-Footstep Guide: Figure Out Who's Hogging Your Bandwidth
 Originally published on April 27, 2017 by
Originally published on April 27, 2017 by
Last updated on March 03, 2022 • 25 minute read
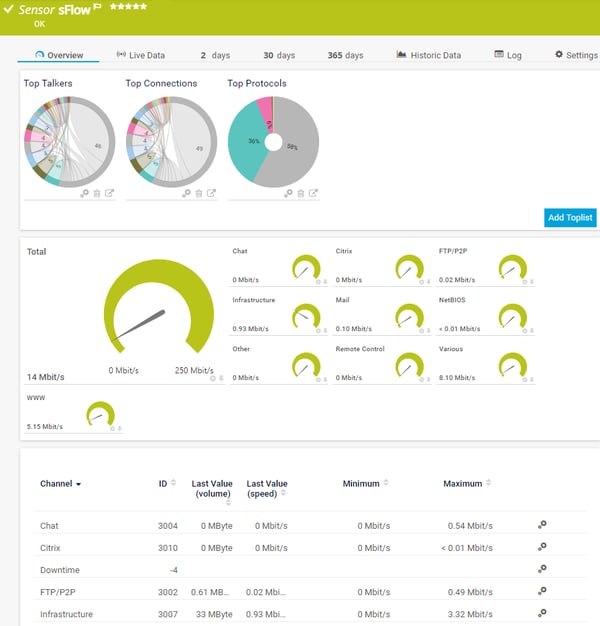
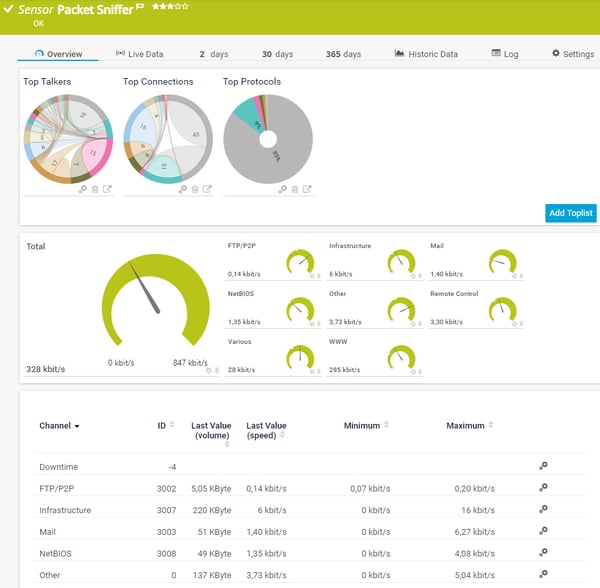
1 of the most mutual (and frustrating!) questions a sysadmin needs to respond is: who is hogging all my bandwidth? The network is slow, users are complaining, and your net connection is at 100% usage (again...). You demand to figure out who or what is hogging all the bandwidth, and y'all demand to do it fast. In this commodity, I'll explain the different methods that are available in different situations, and how to apply SNMP, RMON, menses and packet sniffing to rail down the culprits. The options that are available will depend very much on the hardware you're using, and how much management access you have to that hardware. Kickoff answer yourself the following questions: 1) What type of hardware practice you have? Enterprise-grade hardware offers many more than possibilities than SOHO or consumer-class hardware. Port mirroring, for example, is rarely supported by consumer-form equipment. ii) What hardware vendor(s) exercise you have? Some of the almost useful protocols, such equally netflow, aren't supported past all vendors. So, your ability to monitor bandwidth based on flows is limited to those vendors and models that support menstruum protocols. i NetFlow is a protocol for collecting, aggregating and recording traffic menstruation data in a network. NetFlow data provide a more than granular view of how bandwidth and network traffic are existence used than other monitoring solutions, such as SNMP. NetFlow was adult by Cisco and is embedded in Cisco's IOS software on the visitor's routers and switches and has been supported on almost all Cisco devices since the xi.1 train of Cisco IOS Software. Read more ... 3) How much direction admission practise you accept? You need authoritative admission to the router or switch to enable SNMP or to mirror traffic to an additional port. In a corporate environment, the network administrators volition have full admission to their own equipment, but only limited admission to provider equipment. In a home surround, most customers will have no management access to their Isp router. If y'all don't have management access to the equipment, your options for monitoring are express, and you may need to rely on reporting from the ISP. 4) How many complimentary ports practice you have? Port mirroring (for sniffing) requires an unused port on your switch. If y'all're already actively using all the ports, you'll demand to disconnect something first (not a platonic plan), or you lot won't be able to mirror traffic to a sniffer. So, let's wait at the steps in detail: If your hardware supports it, i of the get-go places to expect is at the device itself. Many devices include detailed traffic statistics as office of their user interface. If you're lucky, your device will report which ports have the most traffic on them, and what IP addresses or protocols are causing this traffic. Example: Cisco SF/SG 200 & 300 Series Example: HP 2920 Serial Port Counters This requires that y'all have plenty direction access to the router to be able to view the statistics, and that the router provides these statistics. If you don't have management access, you tin attempt asking your Internet service provider to generate a report for you. The next line of assault is SNMP, the Due southimple Network Yardanagement Protocol. At that place are standard SNMP metrics to measure out the amount of traffic in/out on each port. These traffic details are included in the "IF_MIB" (Interfaces MIB), which is supported by all major hardware vendors and operating systems. To use SNMP, y'all must outset enable SNMP on your router/switch. The steps to exercise this vary from vendor to vendor, and so please check the documentation from your vendor. Pay attending to two important factors as you're configuring SNMP: what version of SNMP the device supports (v1, v2 or v3), and the read community cord, which is like a password for SNMP. To test that your device is responding to SNMP, y'all tin can use Paessler's free SNMP Tester for Windows. One time the switch is responding to SNMP, you demand a monitoring tool to query your device using SNMP. There are SNMP-based monitoring tools available at all price levels, from freeware to large enterprise platforms. Paessler PRTG, for example, is a unified monitoring tool, including SNMP monitoring, which tin can be run as freeware in a SOHO environment or with a commercial license for corporate environments. Bandwidth monitoring with SNMP volition tell you the corporeality of traffic, over time, on each port. If certain ports have spikes of traffic, you know that the devices connected to those ports are generating a lot of traffic. As an example, here'due south a screenshot of an SNMP traffic sensor from PRTG, showing the amount of traffic in/out, and some additional details well-nigh the type of traffic, such equally unicast versus broadcasts. Example: PRTG SNMP Traffic Sensor The additional data, such every bit the number of broadcasts, can be very useful when debugging network problems. A high number of broadcasts, for example, can signal spanning tree bug. If your spanning tree is constantly recalculating, yous will have recurring network bug. What you think is somebody hogging the network could actually be underlying protocol problems, and so don't ignore these additional counters. 3) RMON Information technology's gone a bit out of fashion, but RMON (Remote MONitoring) is a useful extension to SNMP that you tin can besides consider. If your vendor supports it, RMON adds additional details about the type of traffic yous've got. It was originally developed for monitoring remote sites (hence the name), but can monitor LAN and WAN equipment besides. Since RMON is an extension to SNMP, yous need to have SNMP enabled, and your device needs to support the RMON MIB files. In addition to the SNMP traffic statistics shown above, RMON includes the number of drops, collisions, CRC errors, oversized packets, and much more than. This doesn't tell y'all who'due south hogging your bandwidth, at to the lowest degree not directly. However, issues here (eg. a lot of CRC errors) tell yous that yous have underlying network problems, and then the issue you're trying to track down might exist the network rather than a user. Instance: PRTG SNMP RMON Sensor But let'south become back to looking for the cause of a bandwidth spike... At this indicate, we know from SNMP how much traffic is flowing through a port, and we can encounter which ports accept a lot of traffic on them. If we're lucky, at that place is only ane device attached to a port, and so we know which device is causing all the traffic. Still, at that place could easily exist multiple devices behind that port, and knowing the total traffic from all those devices doesn't tell u.s. which one device is the culprit. To see that, we need to dig deeper into the content of the traffic, and we do that using "flows". The flow protocols are a family unit of protocols that accept one thing in common: they keep track of traffic flowing through the switch and they analyze the data to record things like source/destination IP addresses, source/destination MAC addresses, form of service, IP protocol used, etc. The flow protocols include: A "flow" is like a conversation between two devices. Flow-enabled routers continue rails of each packet they encounter, and create a flow record for each menstruation that they see. The flows are identified by the source IP, destination IP, source port, destination port, and IP protocol. And so, all packets flowing between, say, 10.ten.10.10:80 and 10.200.200.200:51072, brand upwards the one flow betwixt those 2 machines. Catamenia-enabled routers can send data almost the flows they encounter to a menstruum collector device. The menses collector receives information about the flows from multiple devices, and can then create reports about the flows. PRTG, for example, includes flow collectors for NetFlow v5, NetFlow v9, sFlow, jFlow and IPFIX. It then determines "top lists" from the flows: Case: PRTG sFlow Sensor And at present yous tin see the real power of menses monitoring: the height lists tell y'all exactly who or what is using the about bandwidth. Y'all've constitute the culprit! Um, just why is in that location still more than writing beneath? We should be done now, shouldn't we? Well, that depends... Unfortunately, lots of devices don't back up flow, especially lower-terminate equipment. Or, your device might support it, but you don't accept management access to the device to exist able to enable flow monitoring. What and so? At this point, the simply option left is traffic sniffing. That means using some additional device, such as your laptop, to sniff packets and analyze the results. The best fashion to sniff traffic is to configure your router to "mirror" or "span" all of the traffic it sees to an unused port. So you attach your sniffer device (eg. your laptop) to that mirror/span port. Still, this requires authoritative access to the router to configure information technology to beginning mirroring/spanning. (An bated: what's the departure between "mirroring" and "spanning"? None. Cisco calls their mirroring function "Bridge (Switched Port ANalyzer)", which is why the 2 terms have become interchangeable.) If you're able to configure the router to mirror traffic, then you tin adhere a laptop to that port, and then utilize sniffing software to analyze the traffic. If y'all can't configure the router to mirror, and then look for some other device where you *do* have access, that's shut to the target router (from a network signal of view), and sniff on information technology instead. The results won't be perfect, but might still be enough to evidence you what's going on in the network. Yous now need some kind of sniffer software. If y'all'd similar to see superlative lists, similar to netflow, so you tin employ the PRTG "bundle sniffer" sensor to analyze the traffic and produce top lists like to those you lot get from netflow. Case: PRTG Parcel Sniffer Sensor If y'all need more than simply toplists, and thenWireshark is THE gold standard for traffic sniffing. It's not the easiest to learn, just it'south extremely powerful once you've got the hang of information technology. Wireshark offers multiple ways to track downwards bandwidth hogs, for example, under Statistics | Endpoints | IP and and then sort the columns to place the top talkers. Case: Wireshark Endpoints If none of the above has helped, your last line of defense is taps in combination with a package broker. Taps are physical devices that are installed in-line in your network. Because they're in-line, they see all of your traffic and ship copies of the traffic it to a key monitoring device. The monitoring device, called a bundle broker, collects the traffic from all of your taps and forrard it to network monitoring tools for analysis. How Network Taps Piece of work Taps and package brokers are usually too expensive for an SMB to consider. However, consulting companies often offer network analysis based on taps/brokers as a service. So, if you really, really need to rail downwardly a problem, and the steps above haven't helped, y'all can hire someone to temporarily tap the network for you. Installing taps involves temporary interruptions in the network, then this isn't something you desire to do ofttimes. We've now seen all the steps and possible solutions, from easiest to most difficult, that yous tin use to track down bandwidth hogs in your network and to ensure efficient working of your hardware, routers, and fast internet for everyone. Steps for Tracking Downwards Bandwidth Hogs Want To Know More? 1) Look At Statistics On Your Router, Switch Or Firewall
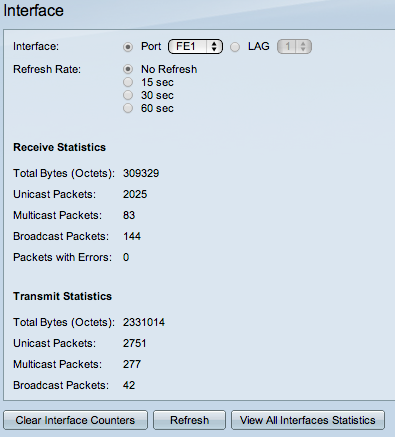
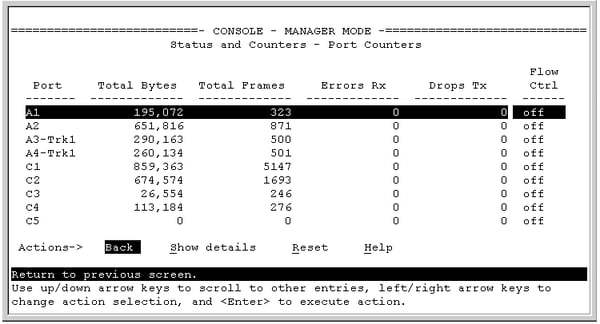
2) SNMP
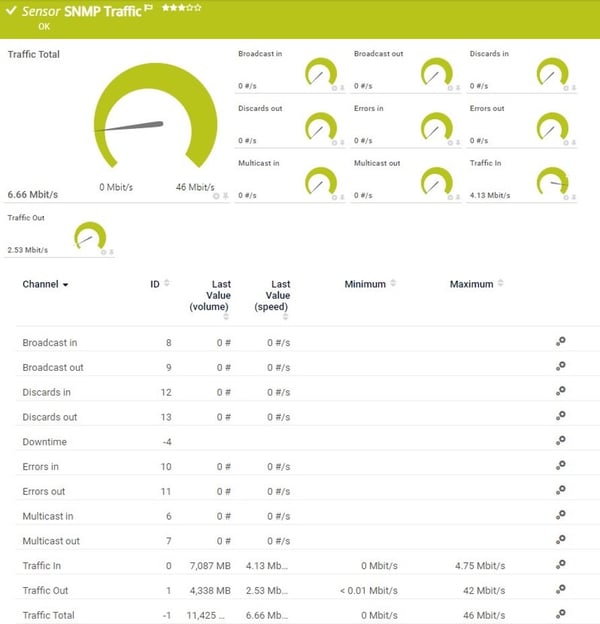
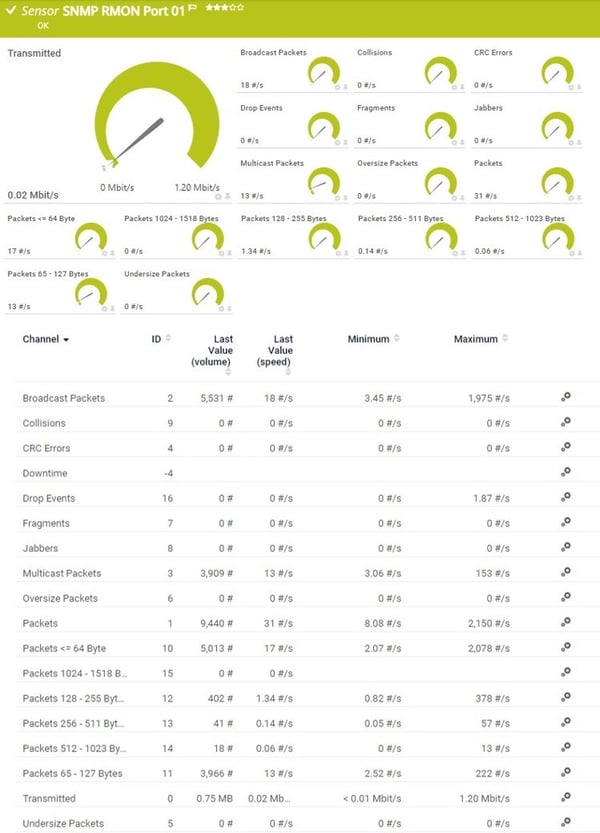
iv) Flow Protocols
5) Packet Sniffing
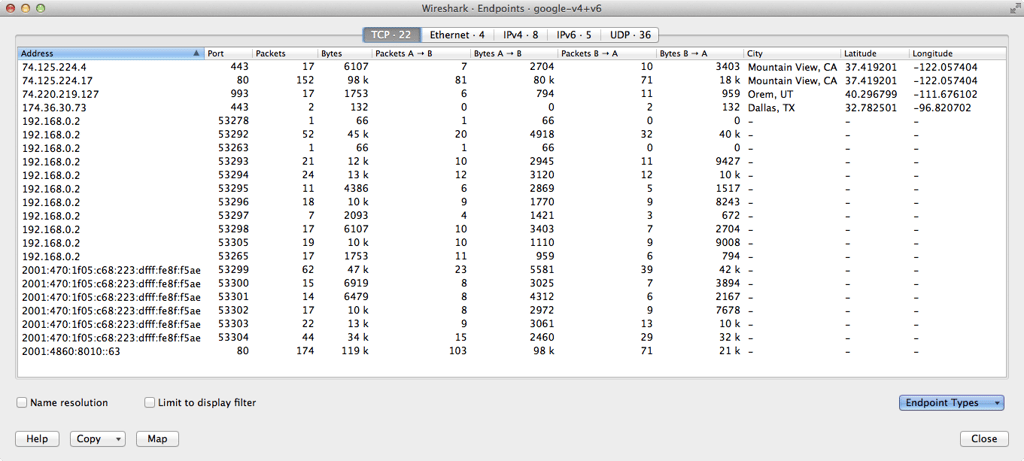
vi) Taps and Packet Brokers

Summary:

All About SNMP:
All Nearly Flows:
All Well-nigh Sniffing, Taps and Packet Brokers:
Source: https://blog.paessler.com/a-step-by-step-guide-figure-out-whos-hogging-your-bandwidth
0 Response to "How to Tell What Is Using Bandwidth on Network"
Post a Comment